People who work with Cisco network equipment need to be able to connect to the console port on their devices. In Windows, you can simply fire up HyperTerminal to get basic access to your devices. If you are using Linux, then you need to know how this can be done with an application called Minicom.
Hardware
First, you are going to need a Cisco console cable, a Cisco device, and a computer. If your computer has a serial port, then you can use the standard console cable that comes with every Cisco device.

If you do not have a serial port (like most new laptops), then you need to purchase a USB to Serial adapter that supports Linux. This device will allow you to use the standard Cisco cable, which has a serial port on one end.
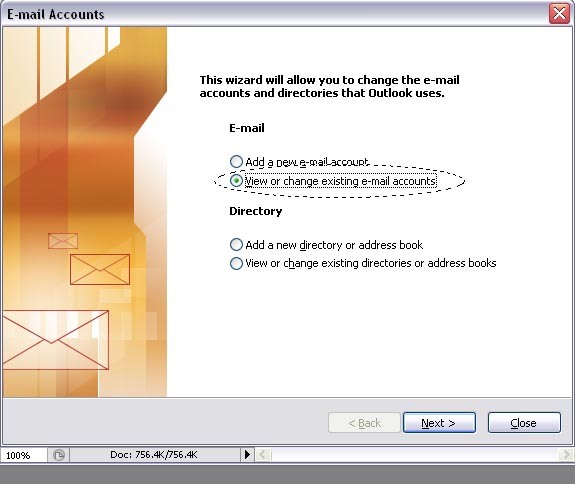
 Install Minicom
Install MinicomYou can easily install Minicom by using "System > Administration > Synaptic Package Manager". Search for "minicom" and choose to install the package. Click "Apply" and Minicom should be installed within a few seconds.

Find the name of your serial port
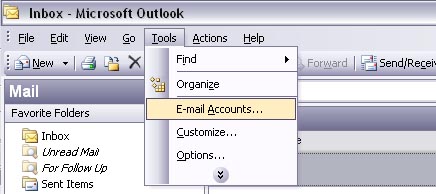
The first thing you need to find out is which device your serial port is mapped to. The easiest way to do this is to connect the console cable to a running Cisco device. Now open up a Terminal using "Applications > Accessories > Terminal" and type this command:
dmesg | grep ttyThe output will look something like this:

Look in this output for words that contain "tty". In this case, it is "ttyS0". That meas the name of the device the corresponds to your serial port is "ttyS0". Now we are ready to configure Minicom to use this information.
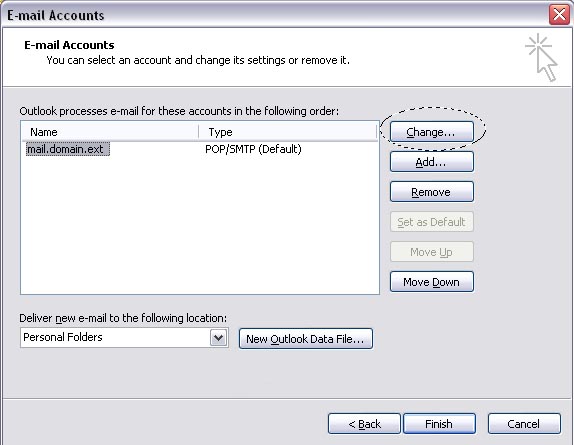
Configure Minicom
Open a terminal using "Applications > Accessories > Terminal". Now type this command to enter the configuration menu of Minicom:
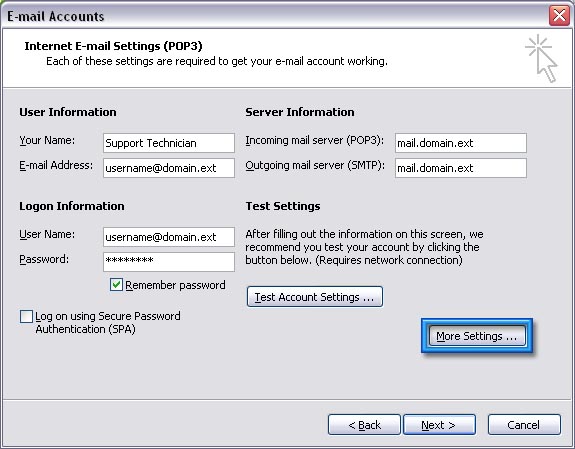
sudo minicom -sUse the keyboard arrow keys to select the menu item labeled "Serial Port Setup" and then hit "Enter". This will open a window that looks similar to the one below:

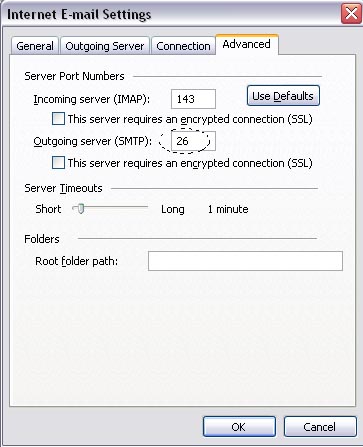
Change your settings to match the ones in the picture above. Here is what I had to change:
- Change the line speed (press E) to "9600"
- Change the hardware flow control (press F) to "No"
- Change the serial device (press A) to "/dev/ttyS0"
- Be sure to use the device name that you learned in the previous step
To find out if you have configured Minicom correctly, type this command in the terminal:
sudo minicomAfter entering your Ubuntu user password, you should be connected to your Cisco device.
Note: You may want to delete the Minicom init string if you see a bunch of gibberish every time you connect to a device. To do this, enter Minicom configuration with:
sudo minicom -sThen select "Modem and dialing". Press "A" to edit the Init string, and delete all characters so that it becomes empty. Make sure you save this to the default profile with "Save setup as dfl". You should no longer see gibberish when you connect to devices.
Create a desktop launcher
If you want to have quicker access to Minicom, you can create a desktop launcher.
- Right-click on the desktop and choose "Create launcher"
- Click on "Icon" and choose the picture you want to use
- Use the "Type" pull-down menu and select "Application in terminal"
- Create a name like "Cisco Console" in the field labeled "Name"
- Enter this command into the field labeled "Command"
- sudo minicom
- Hit "OK" and your desktop launcher is ready for you to use.


I have added this content to the Ubuntu wiki, which you can find here:
https://help.ubuntu.com/community/CiscoConsole
Good day,
What would the device be if you were using a usb -> serial adapter?
Thanks
Andrew
Andrew,
It would probably look something like this:
/dev/ttyUSB0
Hope that helps.
Tristan
Thanks for this tip/howto. I am a sysadmin making the switch to linux desktop and your article really helped. Keep up the good work!!
Wow, thanks for the easy and helpful guide. I got connected to my Cisco gear in the time it took me to read this post.
It would probably look something like this: /dev/ttyUSB0
When I run dmesg | grep tty I get the following and minicom complains that there is no ttyUSB0 when I try to use it.
[ 6.461116] 00:0a: ttyS0 at I/O 0x3f8 (irq = 4) is a NS16550A
[1409448.804000] usb 2-2: FTDI USB Serial Device converter now attached to ttyUSB0
[1409449.128000] usb 2-2: usbfs: interface 0 claimed by ftdi_sio while 'brltty' sets config #1
[1409449.128000] usb 2-2: usbfs: USBDEVFS_CONTROL failed cmd brltty rqt 128 rq 8 len 1 ret -71
[1409454.228000] usb 2-2: usbfs: interface 0 claimed by ftdi_sio while 'brltty' sets config #1
[1409454.232000] ftdi_sio ttyUSB0: FTDI USB Serial Device converter now disconnected from ttyUSB0
[1412269.852000] usb 2-1: FTDI USB Serial Device converter now attached to ttyUSB0
[1412272.068000] usb 2-1: usbfs: interface 0 claimed by ftdi_sio while 'brltty' sets config #1
[1412272.072000] ftdi_sio ttyUSB0: FTDI USB Serial Device converter now disconnected from ttyUSB0
[1497234.816000] usb 2-2: FTDI USB Serial Device converter now attached to ttyUSB0
[1497237.612000] usb 2-2: usbfs: interface 0 claimed by ftdi_sio while 'brltty' sets config #1
[1497237.612000] ftdi_sio ttyUSB0: FTDI USB Serial Device converter now disconnected from ttyUSB0
[1497315.008000] usb 2-2: usbfs: interface 0 claimed by usbfs while 'brltty' sets config #1
[1497380.332000] usb 2-2: usbfs: interface 0 claimed by usbfs while 'brltty' sets config #1
[1497385.764000] usb 2-2: usbfs: interface 0 claimed by usbfs while 'brltty' sets config #1
[1497717.864000] usb 2-2: usbfs: interface 0 claimed by usbfs while 'brltty' sets config #1
[1497723.316000] usb 2-2: usbfs: interface 0 claimed by usbfs while 'brltty' sets config #1
Sidenote and possible issue....I have VMWare Server installed and when I run dmesg alone I see many calls to vmware and usbfs as shown below:
[1497948.908000] usb 2-2: usbfs: process 20365 (vmware-vmx) did not claim interface 0 before use
[1497953.944000] usb 2-2: usbfs: process 20365 (vmware-vmx) did not claim interface 0 before use
[1497958.936000] usb 2-2: usbfs: process 20365 (vmware-vmx) did not claim interface 0 before use
[1497963.968000] usb 2-2: usbfs: process 20365 (vmware-vmx) did not claim interface 0 before use
Any suggestions?
Al